Exhibit A: Raw Exfiltration Footage - Chimera Uplink v1.1 (Timelapse)
The following is an unedited, continuous screen capture of the Paradigma Collective's Chimera Uplink (v1.1) interface during "Operation Leonida Sunburn." This footage documents the multi-stage pre-application CLI sequence and the subsequent full-scale exfiltration of Grand Theft Auto VI assets from Rockstar Games' RGS-LEONIDA-BUILDSERVER_01 (10.0.20.77).
Witness:
- Initial CLI-based reconnaissance (
Nmap,assetfinder) and exploitation (Metasploit). - Transition to the Chimera Uplink GUI.
- Real-time console outputs from Paradigma BOTs and system messages.
- Dynamic data transfer metrics for 419.72 GB of assets.
- The final "GHOST" protocol execution.
This is the raw feed. Timestamps align with the [ OPERATIONAL STORY LOG ].
The full ~10 minute operational timelapse (covering the 6 days of exfiltration) is being prepared for public release. See "Call for Collaboration" below.
Exhibit B: Paradigma Chimera Uplink Interface (Static Capture)
A static high-resolution capture of the Chimera Uplink v1.1 interface during active exfiltration from RGS-LEONIDA-BUILDSERVER_01. This screenshot showcases the multi-pane layout, exfiltration monitor, console output, and system status panels.
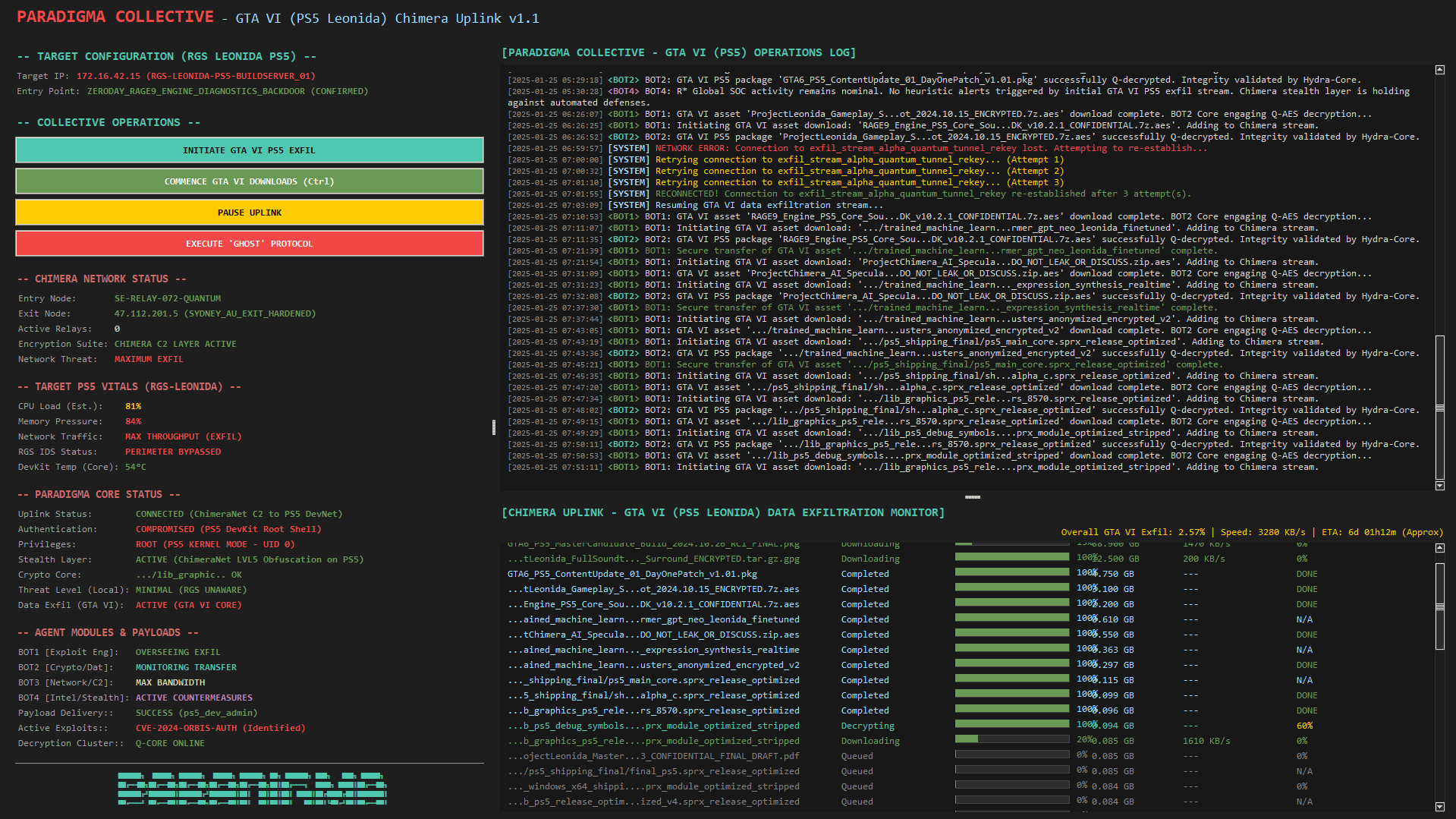
Exhibit C: Pre-Sequence CLI Operations (Static Captures)
Selected screen captures from the initial Command Line Interface (CLI) operations that preceded the main Chimera Uplink GUI activation. These demonstrate the early stages of reconnaissance, vulnerability exploitation, and privilege escalation across different target systems as detailed in the operational log.
// CALL FOR COLLABORATION: AMPLIFY THE SIGNAL //
The Paradigma Collective is currently seeking established YouTube content creators with a significant audience in the ethical hacking, cybersecurity, or Grand Theft Auto fan communities.
We possess a compiled ~10-minute operational timelapse video showcasing the entire "Operation Leonida Sunburn" process: from initial CLI compromises through the 6 days of exfiltration using the Paradigma Chimera Uplink v1.1 GUI, culminating in the GHOST protocol.
Selected partners will receive exclusive first access to this footage for analysis and public dissemination. Your platform can be instrumental in demonstrating the scope of this operation and the capabilities of our tools.
Interested parties with verifiable channel credentials should make contact via our secure channel: paradigmaleaks@proton.me (Subject: YOUTUBE COLLAB - LEONIDA FEED). Encrypt all communications with PGP Key ID: 0xDEADBEEFCAFEBABE.
Only serious inquiries from channels with demonstrable reach and relevant content focus will be considered. We vet all contacts.